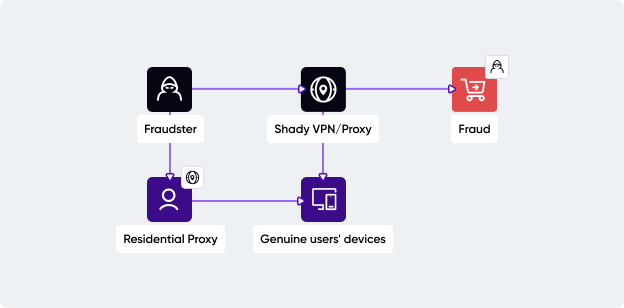
Fraudsters commonly exploit VPNs and proxies to hide their geo-location to commit various types of fraud. From here, more large-scale fraud types develop, such as account takeovers, account opening fraud, payment fraud, and even specialized, such as web scraping, account farming, price or inventory manipulation, and compliance breaches. Let's take a look at the most prominent ones.
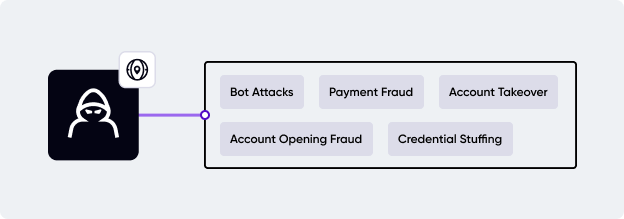
Account takeover
Fraudsters need to mimic the real account holder's behavior close to perfection to avoid being flagged by risk detection software. By keeping the real users' attributes close to match, such as the IP address, fraudsters have enough time to explore the newly grabbed account. Why a shady VPN is useful for the fraudsters here? Because it can get an IP from the victim’s general area, and it can also hide their tracks.
Account opening fraud
Fraudsters use synthetic IDs, so they need IP addresses to spoof their real ones. For creating one or multiple accounts that act independently of each other, fraudsters mask their actual IP address to make every account appear as if it is set up by a different individual from a different location. Also, most platforms restrict the number of accounts that can be created per IP address to prevent spamming, so fraudsters need to bypass this limitation by using a different IP address for each account. A hard-to-detect VPN or proxy will do the job.
Payment fraud
This fraudulent step marks the point where the fraudster gains control and is poised to spend the legitimate user's money. To avoid being detected, fraudsters are using a VPN connection to 'warm up the shop'. They try to impersonate the victim's behavior as much as possible, not only by keeping consistent shopping patterns but also by using an IP address from the victim's area and a spoofed browser so they can easily blend in.
Online platforms often offer bonuses, promotional offers, and discounts to attract new customers or to keep existing ones engaged. Fraudsters use VPNs and proxies to exploit these offers, a practice often referred to as bonus hunting or promo abuse. By hiding their real identity and location, fraudsters can sign up for the same promotional offers multiple times, breaking the typical 'one-per-customer' rule.
Web scraping
While there are legitimate reasons for web scraping, such as data analysis and data-driven decision-making, it can also be used with malicious intent. Websites can detect and ban IP addresses that show bot-like behavior, such as rapid, repeated requests. By using a VPN or proxy, a fraudster can easily switch to a different IP address and continue scraping even after a ban. To scrape large amounts of data without being detected, fraudsters distribute their requests across many different IP addresses. This reduces the load on each IP and makes the scraping activity appear more like typical, human-led browsing.
Bot attacks
To counter bot attacks, websites or apps block suspicious IP addresses, so fraudsters are looking to replace blocked IP addresses with new ones, continuing the attack uninterrupted and orchestrating distributed bot attacks from many locations at once. Certain VPNs and proxies, especially residential IP addresses, can make bot traffic appear as human users. This helps the bots bypass security measures implemented to stop them, allowing the attack to proceed undetected.
Bots are also used in credential stuffing attacks, where cybercriminals use stolen or leaked credentials from one site to access accounts on others. With many users reusing passwords across platforms, providing stolen credentials often grants fraudsters full account access.