- Product
- Product overview
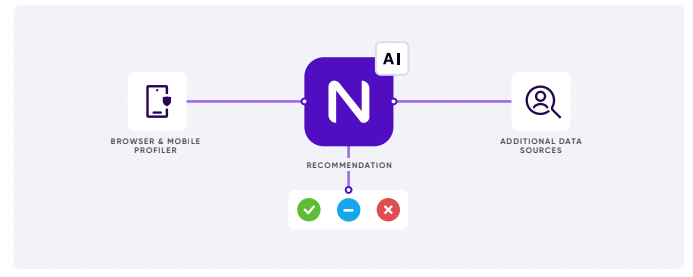
- Risk detection
- Dashboard with decision engine
- Machine learning models
- Data enrichment
- Nethone KYC
- Nethone Alerts
- Order Insights with CE 3.0 provided by Nethone
- Customer success
- Online transaction fraud
- Account takeover
- Identity verification
- Policy and promo abuse
- PSD2 SCA compliance
- Use cases
- Pricing
- Resources
- About
Product
Issues we resolve
Protect your customers’ online payment experiences across web and mobile
Proven ATO prevention from start to finish of every customer journey
Verify your customers and assess fraud risk in one go
Identify fraudsters and true intentions of dishonest customers to prevent abuse
Frictionless PSD2 SCA compliance without a fall in security
Industries
User’s Lifecycle
KYC/AML compliance, affiliate fraud, promo abuse
Account takeover (ATO)
Payment fraud, resell abuse, return/refund fraud
Chargeback disputes, return/refund abuse
About
General Contact
Career Opportunities
Media Inquries
- Product
- Product overview
- Risk detection
- Dashboard with decision engine
- Machine learning models
- Data enrichment
- Nethone KYC
- Nethone Alerts
- Order Insights with CE 3.0 provided by Nethone
- Customer success
- Online transaction fraud
- Account takeover
- Identity verification
- Policy and promo abuse
- PSD2 SCA compliance
- Use cases
- Pricing
- Resources
- About
Product
Issues we resolve
Protect your customers’ online payment experiences across web and mobile
Proven ATO prevention from start to finish of every customer journey
Verify your customers and assess fraud risk in one go
Identify fraudsters and true intentions of dishonest customers to prevent abuse
Frictionless PSD2 SCA compliance without a fall in security
Industries
User’s Lifecycle
KYC/AML compliance, affiliate fraud, promo abuse
Account takeover (ATO)
Payment fraud, resell abuse, return/refund fraud
Chargeback disputes, return/refund abuse
About
General Contact
Career Opportunities
Media Inquries

.png?width=1200&height=324&name=ATO%20Course%20Banner%20(3).png)
.png?width=1000&height=270&name=ATO%20Course%20Banner%20(3).png)
.jpg?width=1200&height=324&name=ATO%20Course%20Banner%20(1).jpg)