What is a behavioral biometric, with an example?
A behavioral biometric is a parameter or other micropattern that is near-unique to a given user, based on an analyse of historical data. For example, how a user types includes numerous frequent keystroke combinations, as well as their overall timing and speed, that can be used to verify a customer's identity.
What is the most commonly used type of behavioral biometrics?
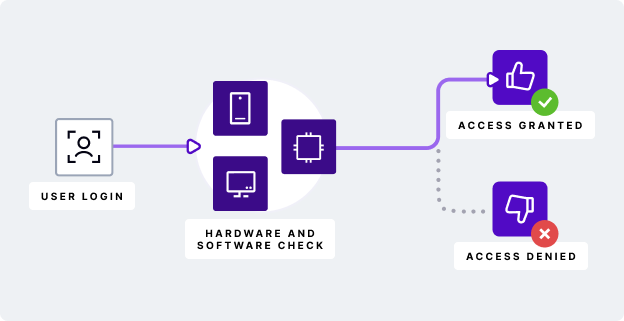
The most common behavioral biometrics are based on a user's physical input. This includes how they type, how they use their mouse and/or mobile device. The way in which they navigate or type provides numerous micropatterns that can be analyzed. There are often paired with a user's digital fingerprint - where they are logging in from and on which specific device - to build known patterns and behaviors.
What are the instances of behavioral biometrics?
There are many use cases and instances of behavioral biometrics in business. They are most commonly used to provide account takeover protection. Such instances are most commonly applied during payments, so they are most active on ecommerce stores, mobile banking apps, social media platforms and more.
What are physical vs behavioral biometrics?
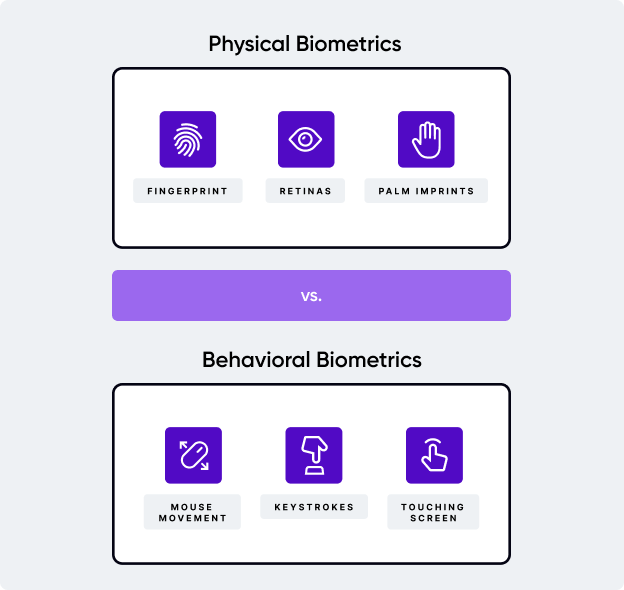
While both are useful, we can separate behavioral biometrics and physical biometrics by the data being recorded. Behavioral biometrics analyze parameters that result due to a user's physical actions. This includes their keystrokes, navigational patterns, cursor movements and more. Physical biometrics, on the other hand, relate to direct physiological biometrics and features, such as retinas and fingerprints.
Why are behavioral biometrics important?
Behavioral biometrics are important because they monitor and measure data points that are significantly more difficult, if not impossible, for potential fraudsters to detect. While passwords and other authentication measures only block or allow access, behavioral analytics considers the users behavior from start to finish, providing a greater chance for fraudsters to be detected and further limit any potential damage.
What are the ethical issues in behavioral biometrics?
Due to their nature in data collection, there are some ethical issues associated with behavioral biometrics in regards to security and privacy. The main criticisms stem from the fact that behavioral biometrics collect data unique to each individual, which some may regard as an invasion of privacy. Many others, however, argue that the convenience of behavioral biometric authentication as a passive technology makes such concerns a fair trade in comparison to more abrupt active technology.
In more extreme cases, some argue that the nature of biometric technologies designed to capture such data, may lead to subsequent technologies designed to replicate the behavior at an advanced enough level to trick the original systems.
What is an example of behavioral data?
Keystroke dynamics are a common example of behavioral data. It consists of data regarding the speed, efficiency and frequency in which individual users log keystrokes. With enough historical data, this creates a pattern generated by the users own behavior, which is in turn unique to them and can be used to mark them as a legitimate user of their own account.
What are the benefits of behavioral biometrics?
The main advantages of behavioral biometrics are that it runs automatically, is unique to each individual user and expands as more historical data is generated. All of this makes it very hard to bypass, giving user accounts an extra layer of protection against identity theft and account takeover fraud.
What is behavioral biometrics for continuous authentication?
Behavioral biometric authentication occurs in the background of services and remains active doing an entire session. Unlike other protective layers, such as passwords, this continuous authentication continues to monitor and authenticate users throughout their session.
What are behavioral biometrics in banking?
In banking and other financial institutions, behavioral biometrics authentication is used as an automated and scalable way to assess the risk of a potential fraudulent account. Behavioral biometrics track the behavior of each user on banking websites, apps and other digital services, gaining a unique understanding of each person. When new behavior strays too far from the historical prediction, banks can implement a number of automatic strategies to limit identity fraud.
This is often combined with digital fingerprint - the location of the user, the device they use and other physical metrics - to authenticate identity at a granular, individual level. Together, they are common elements in both typical desktop access, mobile banking and even card payments.
What are some potential benefits of using behavioral biometrics authentication?
Due to the vast possible data points, biometrics are incredibly hard, if not impossible, for identity thieves to replicate successfully. As a passive form of technology, behavioral biometrics can also run continuously in the background, monitoring for threats even when other means, such as passwords, have been bypassed. What's more, their passive nature doesn't require input from the user, and neither does it impact the overall experience or usability of online services. All of these make biometrics are very scalable and adapting solution.

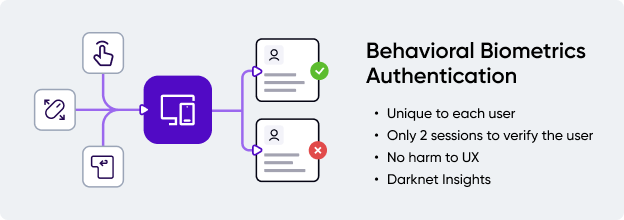

 When it comes to fraud prevention, behavioral biometric authentication considers all of the above criteria to determine the validity of the user. As a form of multi factor authentication, it provides an extra step for identity thieves to overcome.
When it comes to fraud prevention, behavioral biometric authentication considers all of the above criteria to determine the validity of the user. As a form of multi factor authentication, it provides an extra step for identity thieves to overcome.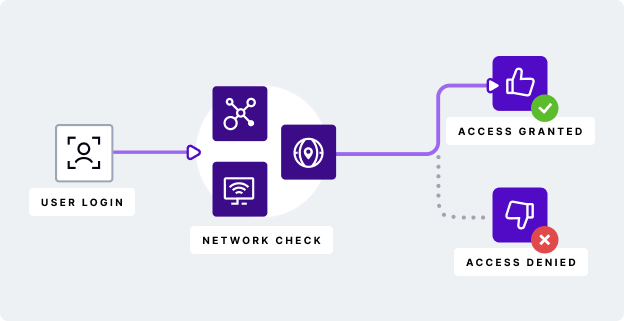
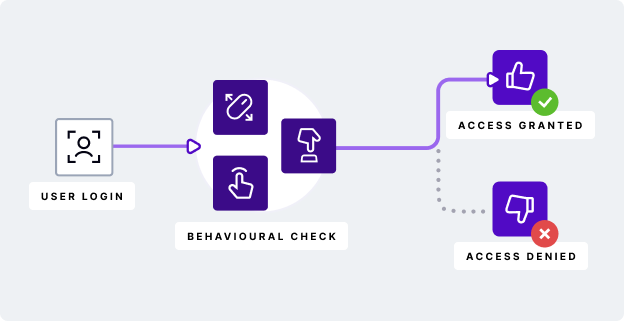
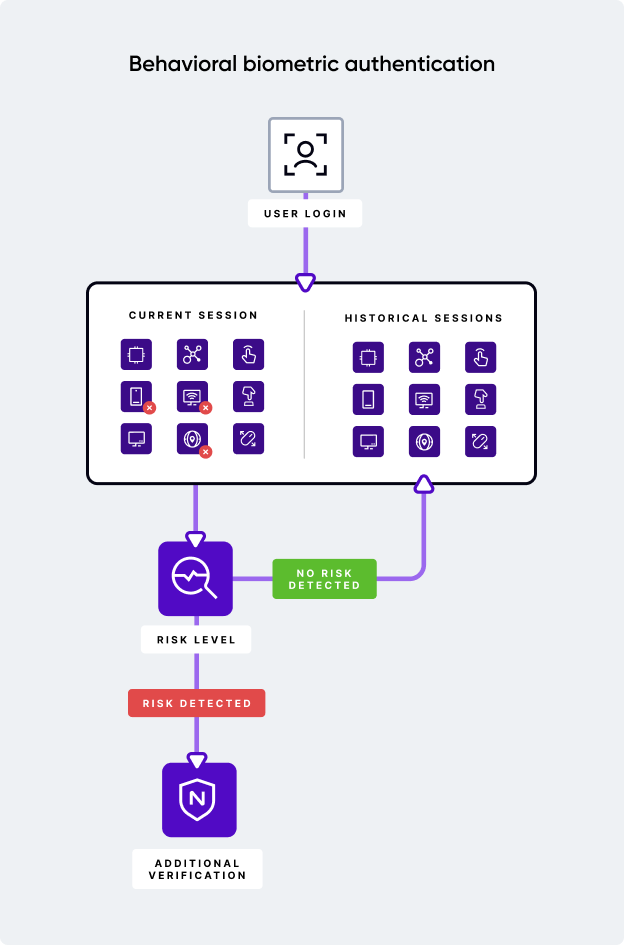
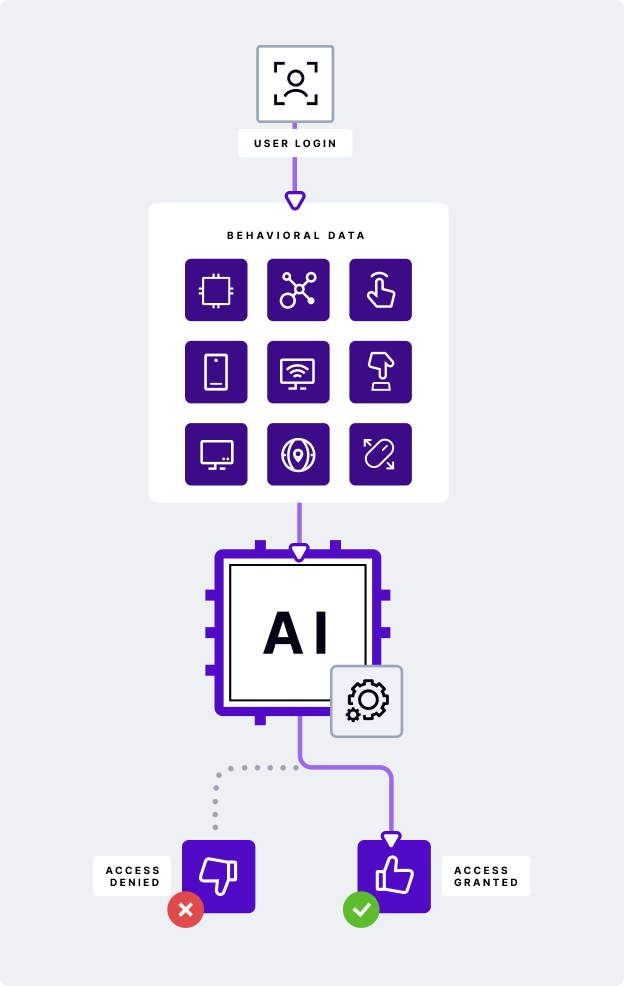 Wrapping things up, behavioral biometrics powered by AI, increases the precision of identity theft detection, including in instances where fraudsters are using Remote Access Tools (RATs), shady VPNs, or other fraud tools used to mask their identity or manipulate other data attributes from network. Combining the unique user behavior with the context network, this dyanimc duo can detect even the slightest anomaly when users log into their account. And the best part? It all happens passively in the background, with no harm to UX.
Wrapping things up, behavioral biometrics powered by AI, increases the precision of identity theft detection, including in instances where fraudsters are using Remote Access Tools (RATs), shady VPNs, or other fraud tools used to mask their identity or manipulate other data attributes from network. Combining the unique user behavior with the context network, this dyanimc duo can detect even the slightest anomaly when users log into their account. And the best part? It all happens passively in the background, with no harm to UX.
