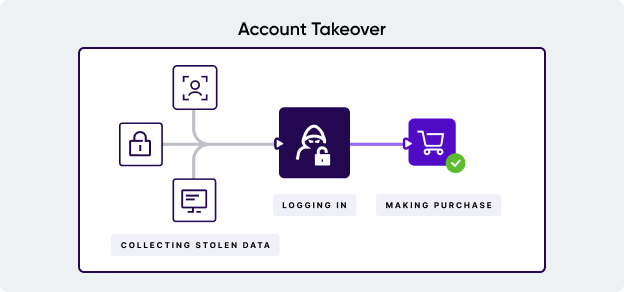
One critical step in preventing account takeover fraud is understanding how access is gained in the first place. There are many ways in which bank account takeover fraud occurs, from singular targeted attacks to large scale operations.
Data breaches
If a corporate account is targeted, it opens up a treasure trove of crucial information about the bank's customers. Sometimes, this can include all the credentials needed to gain entry, while, in others, it might include some key information, such as email addresses, that can then be combined with other methods on this list.
Such a data breach doesn't need to be committed by the fraudster directly, either. Data breaches are often orchestrated by individuals who then peddle the compromised information online – often in the seedy corners of the dark web – giving the opportunity for further exploitation by other fraudsters.
Brute force attacks
Also known as dictionary attacks, this approach sees cybercriminals attempting different combinations of letters and numbers, combined with known email addresses, to guess passwords. This strategy utilizes a lot of bots to scale effectively.
Social engineering
Social engineering methods are the real plague of banking fraud. When it comes to individual bank accounts, fraudsters can deploy a number of scams to collect passwords and account details from users. Common methods include:
- Pretending to be a user's bank via fake social media accounts, phishing emails or phone calls. In these cases, fraudsters try to convince the user to reveal critical information they can then use to gain access.
- Creating a fake website designed to look like the real bank's website. In this approach, users submit their login credentials and are then directed to the real service. The fraudster then has the details, and the user is none the wiser to the ATO fraud.
These processes are also often known as "man in the middle" approaches. During this kind of attack, the fraudster relays communication between the user and the bank. As the information is still delivered to the bank, the user achieves their expected outcome, leaving the bank oblivious to the ongoing fraud.

Credential stuffing
As mentioned before, if login credentials don't differ between accounts, this could allow fraudsters to exploit that information to access online banking as well. Dedicated cybercriminals will take stolen credentials that they know work on one platform, and attempt to use them on as many other platforms as possible to find new vulnerable accounts.
Viruses and malware
Fraudsters can also gather sensitive information through keylogging malware. One popular method involves mobile banking trojans in the form of apps designed to represent a legitimate bank's application. Other forms can include sending files through email or websites, often combined with phishing attacks.

.png?width=861&height=202&name=CTA%20%233%20(3).png)

 < Check in details:
< Check in details: 